- Openswan 2.4.15
- Sonicwall Firmware 5.2.0.1-21o
- /etc/ipsec/ipsec.conf
- /etc/ipsec/ipsec.secrets
I found a few tutorials on how to do this on google, but none seemed to work without changing things found in another tutorial. Here are a few for reference:
Needless to say, I had a lot of trial and error, but I got things working (in a way I think is better than the tutorials I found). I was able to rid my configuration files of hardcoded IP addresses for my laptop so that I can use this from anywhere. First off, let's start with the configuration needed on the Sonicwall Firewall itself.
Login to your Sonciwall and go to the "VPN" section. You'll see a screen similar to this:
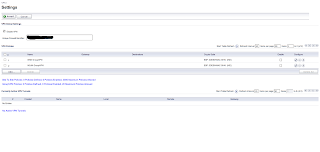 Take note of the "Unique Firewall Identifier" text box. You will need to know that value for later. Go ahead and click on the pencil icon next to "WAN GroupVPN" to edit it's settings. You'll end up with a window that looks like this:
Take note of the "Unique Firewall Identifier" text box. You will need to know that value for later. Go ahead and click on the pencil icon next to "WAN GroupVPN" to edit it's settings. You'll end up with a window that looks like this: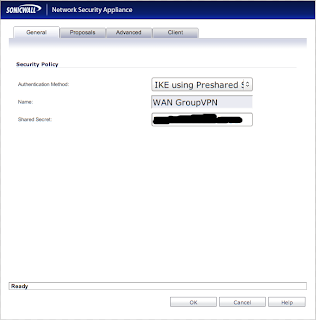
You need to be sure that "Authentication Method" is set to "IKE using Preshared Secret". Take note of the value that is in the "Shared Secret" text box. You'll need it later. Now click the "Proposals" tab to get a new window:
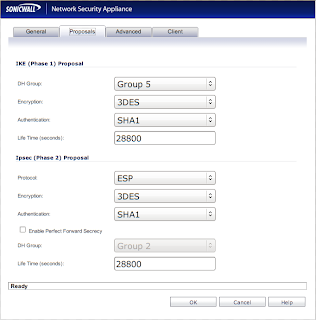 All your settings should reflect the screenshot, however, I'm pretty sure that "Life Time" can be whatever you want. Now click the "Advanced" tab to go to a new screen:
All your settings should reflect the screenshot, however, I'm pretty sure that "Life Time" can be whatever you want. Now click the "Advanced" tab to go to a new screen: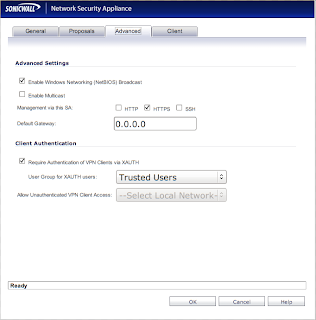
Check to be sure that the "Require Authentication of VPN Clients via XAUTH" box is checked. Also be sure that you have a valid user that belongs to whatever group you specify for "User Group for XAUTH users".
That takes care of the Sonicwall configuration, so now let's go back to your desktop/laptop machine.
Install a copy of Openswan to get the ball rolling. I use Gentoo, so the command for me is
emerge openswan
The fun part really comes in setting up your configuration files, so be prepared to use your favorite text editor. Go ahead and edit "/etc/ipsec/ipsec.conf". The contents of the file should be like what I have below (using the comments as a guide). REMOVE THE COMMENTS IN YOUR OWN FILE!!!! If you leave them there, you WILL have problems.
#/etc/ipsec/ipsec.conf
config setup
plutodebug="none"
klipsdebug="none"
nat_traversal=yes
nhelpers=0
interfaces = %defaultroute
conn MyVPN # Arbitrary connection name.
type=tunnel
left=%defaultroute # The interface to use from the client. %defaultroute
# automatically selects an interface for you.
leftid=@GroupVPN # An arbitrary name to call your ID. The "@" is required.
leftxauthclient=yes # Use XAUTH for connecting
right=firewall.domain.com # The FQDN/IP of the VPN server (Sonicwall)
rightsubnet=192.168.168.0/24 # The subnet of the internal VPN interface on the Sonicwall
# (ie. The subnet you should be on after connecting)
rightxauthserver=yes # Use XAUTH for authentication
rightid=@0078F89ABF # The "Unique Firewall Identifier" from the Sonciwall
# (usually the serial number of the Sonicwall). "@" is required.
keyingtries=1
auto=add
auth=esp
esp=3des-sha1
ike=3des-sha1-modp1536
xauth=yes
pfs=no
authby=secret
aggrmode=yes
include /etc/ipsec/ipsec.d/examples/no_oe.conf
Now that the main configuration file is finished, we need to create "/etc/ipsec/ipsec.secrets". That file is what stores the PSK (Pre Shared Key) that you saw earlier in the Sonicwall configuration. There will be line like:
@<leftid_from_ipsec.conf> @<rightid_from_ipsec.conf> : PSK "<my_psk>"
#/etc/ipsec/ipsec.secrets
@GroupVPN @0078F89ABF : PSK "MySharedSecret"
With those two files out of the way, you should be ready to connect now! First, be sure that the ipsec service is started by running "/etc/init.d/ipsec start".
Now you can start your VPN connection by running "ipsec auto --up MyVPN" where "MyVPN is the name of your connection in "/etc/ipsec/ipsec.conf".
Assuming that everything worked, you will be asked for your username and password after which the Sonicwall will connect you. To bring the connection down run "ipsec auto --down MyVPN".
If you ever want to change the connection configuration after the ipsec server is started, just run "ipsec auto --add MyVPN". That will reread the configuration file for changes to the "MyVPN" connection.
I hope that this saves you from hours of trial and error!
2 comments:
I would like to ask you some questions regarding your configuration with Openswan and Sonicwall.
Stephen: Go ahead. It has been a while since I've worked on this though. I also no longer work at the company where I used this, so any answers will have to be from memory.
Post a Comment